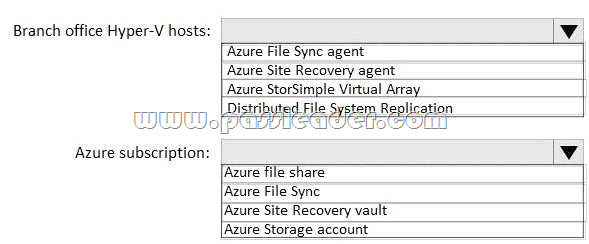
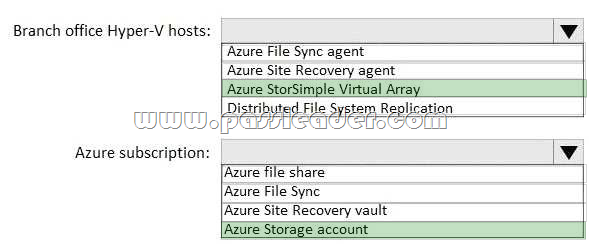
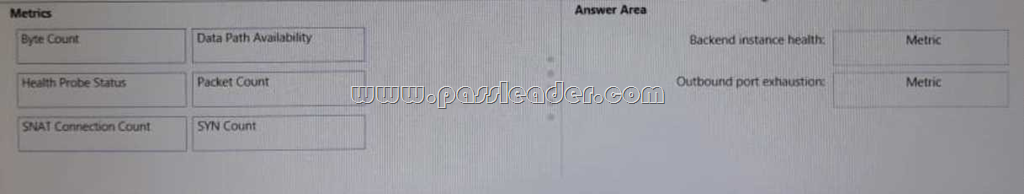
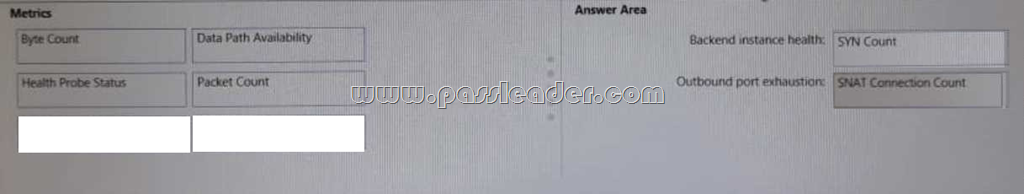
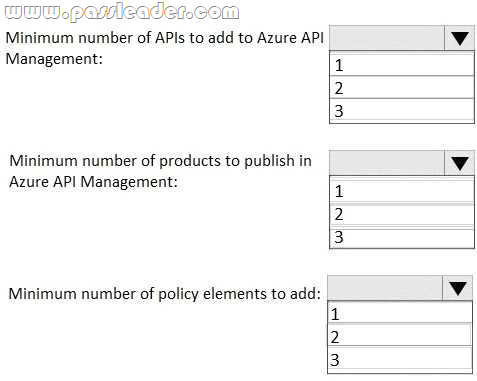
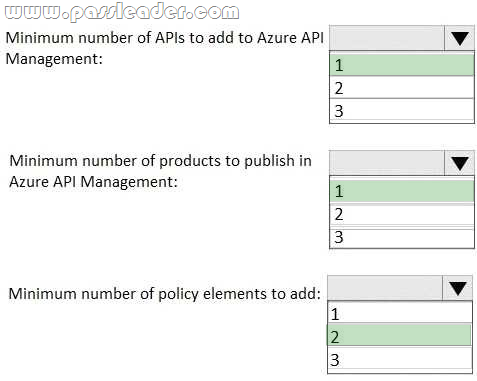
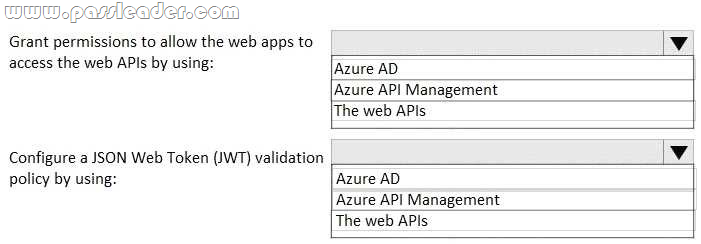
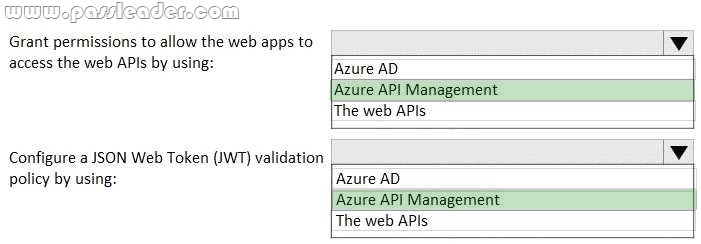
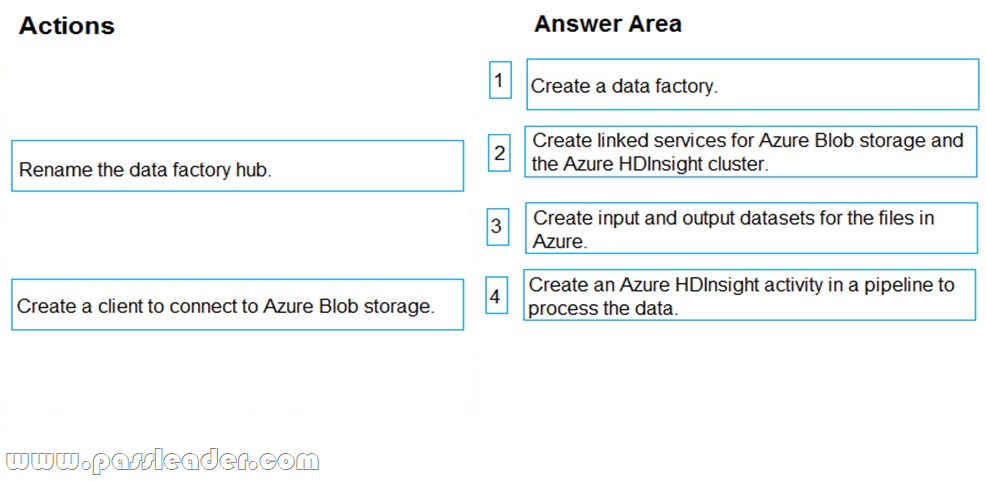
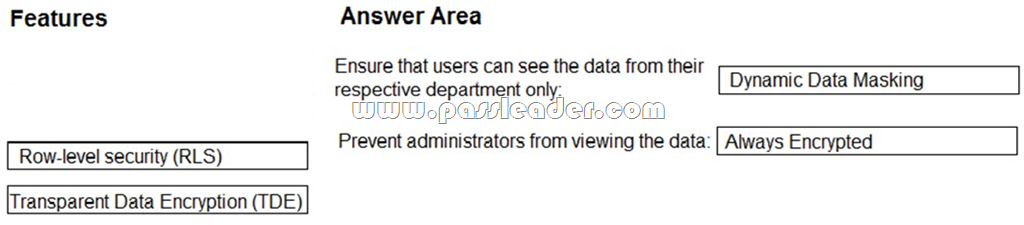
New Updated 312-50v10 Exam Questions from PassLeader 312-50v10 PDF dumps! Welcome to download the newest PassLeader 312-50v10 VCE dumps: https://www.passleader.com/312-50v10.html (772 Q&As)
Keywords: 312-50v10 exam dumps, 312-50v10 exam questions, 312-50v10 VCE dumps, 312-50v10 PDF dumps, 312-50v10 practice tests, 312-50v10 study guide, 312-50v10 braindumps, Certified Ethical Hacker v10 Exam
P.S. New 312-50v10 dumps PDF: https://drive.google.com/open?id=1_ULihyLPLTBI_LfyL2UePVvTPFp3Vws-
P.S. New 312-50v9 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpdnh4LVZhSV9hYm8
P.S. New 312-49v9 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpSnJrVWZSSFFMVVE
NEW QUESTION 701
A company’s security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
A. Attempts by attackers to access the user and password information stored in the company’s SQL database.
B. Attempts by attackers to access Web sites that trust the Web browser user by stealing the user’s authentication credentials.
C. Attempts by attackers to access password stored on the user’s computer without the user’s knowledge.
D. Attempts by attackers to determine the user’s Web browser usage patterns, including when sites were visited and for how long.
Answer: B
NEW QUESTION 702
To maintain compliance with regulatory requirements, a security audit of the systems on a network must be performed to determine their compliance with security policies. Which one of the following tools would most likely be used in such an audit?
A. Protocol analyzer
B. Intrusion Detection System
C. Port scanner
D. Vulnerability scanner
Answer: D
NEW QUESTION 703
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist’s email, and you send her an email changing the source email to her boss’s email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network. What testing method did you use?
A. Social engineering
B. Piggybacking
C. Tailgating
D. Eavesdropping
Answer: A
NEW QUESTION 704
Your team has won a contract to infiltrate an organization. The company wants to have the attack be as realistic as possible; therefore, they did not provide any information besides the company name. What should be the first step in security testing the client?
A. Reconnaissance
B. Escalation
C. Scanning
D. Enumeration
Answer: A
NEW QUESTION 705
A medium-sized healthcare IT business decides to implement a risk management strategy. Which of the following is NOT one of the five basic responses to risk?
A. Accept
B. Delegate
C. Mitigate
D. Avoid
Answer: B
NEW QUESTION 706
OpenSSL on Linux servers includes a command line tool for testing TLS. What is the name of the tool and the correct syntax to connect to a web server?
A. openssl s_client -site www.website.com:443
B. openssl_client -site www.website.com:443
C. openssl_client -connect www.website.com:443
D. openssl s_client -connect www.website.com:443
Answer: D
NEW QUESTION 707
Which of the following describes the characteristics of a Boot Sector Virus?
A. Modifies directory table entries so that directory entries point to the virus code instead of the actual program.
B. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR.
C. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR.
D. Overwrites the original MBR and only executes the new virus code.
Answer: C
NEW QUESTION 708
John is an incident handler at a financial institution. His steps in a recent incident are not up to the standards of the company. John frequently forgets some steps and procedures while handling responses as they are very stressful to perform. Which of the following actions should John take to overcome this problem with the least administrative effort?
A. Increase his technical skills.
B. Read the incident manual every time it occurs.
C. Select someone else to check the procedures.
D. Create an incident checklist.
Answer: D
NEW QUESTION 709
Which of the following is the least-likely physical characteristic to be used in biometric control that supports a large company?
A. Voice
B. Fingerprints
C. Iris patterns
D. Height and Weight
Answer: D
NEW QUESTION 710
While using your bank’s online servicing you notice the following string in the URL bar:
“http://www.MyPersonalBank.com/account?id=368940911028389&Damount=10980&Camount=21″
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes. Which type of vulnerability is present on this site?
A. Cookie Tampering
B. SQL Injection
C. Web Parameter Tampering
D. XSS Reflection
Answer: C
NEW QUESTION 711
It is an entity or event with the potential to adversely impact a system through unauthorized acces, destruction, disclosure, denial of service or modification of data. Which of the following terms best matches the definition?
A. Attack
B. Vulnerability
C. Threat
D. Risk
Answer: C
NEW QUESTION 712
Which of the following is one of the most effective ways to prevent Cross-site Scripting (XSS) flaws in software applications?
A. Use security policies and procedures to define and implement proper security settings.
B. Use digital certificates to authenticate a server prior to sending data.
C. Validate and escape all information sent to a server.
D. Verify acces right before allowing access to protected information and UI controls.
Answer: C
NEW QUESTION 713
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
A. Armitage
B. Nikto
C. Metasploit
D. Nmap
Answer: B
NEW QUESTION 714
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines in Evil Corp’s lobby. He checks his current SID, which is S-1-5-21-1223352397-1872883824-861252104-501. What needs to happen before Matthew has full administrator access?
A. He needs to gain physical access.
B. He must perform privilege escalation.
C. He already has admin privileges, as shown by the “501” at the end of the SID.
D. He needs to disable antivirus protection.
Answer: B
NEW QUESTION 715
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He is determined that the application is vulnerable to SQL injection and has introduced conditional timing delays into injected queries to determine whether they are successful. What type of SQL injection is Elliot most likely performing?
A. NoSQL injection
B. Blind SQL injection
C. Union-based SQL injection
D. Error-based SQL injection
Answer: B
NEW QUESTION 716
You have successfully logged on a Linux system. You want to now cover your track. Your login attempt may be logged on several files located in /var/log. Which file does NOT belong to the list?
A. wtmp
B. user.log
C. btmp
D. auth.log
Answer: B
NEW QUESTION 717
When you return to your desk after a lunch break, you notice a strange email in your inbox. The sender is someone you did business with recently, but the subject line has strange characters in it. What should you do?
A. Forward the message to your company’s security response team and permanently delete the message from your computer.
B. Reply to the sender and ask them for more information about the message contents.
C. Delete the email and pretend nothing happened.
D. Forward the message to your supervisor and ask for her opinion on how to handle the situation.
Answer: A
NEW QUESTION 718
The “gray box testing” methodology enforces what kind of restriction?
A. Only the internal operation of a system is known to the tester.
B. The internal operation of a system is completely known to the tester.
C. The internal operation of a system is only partly accessible to the tester.
D. Only the external operation of a system is accessible to the tester.
Answer: C
NEW QUESTION 719
Log monitoring tools performing behavioral analysis have alerted several suspicious logins on a Linux server occuring during non-business hours. After further examination of all login activities, it is notices that none of the logins have occurred during typical work hours. A Linux administrator who is investigating this problem realized the system time on the Linux server is wrong by more than twelve hours. What protocol used on Linux serves to synchronize the time has stopped working?
A. NTP
B. TimeKeeper
C. OSPF
D. PPP
Answer: A
NEW QUESTION 720
The “black box testing” methodology enforces what kind of restriction?
A. Only the internal operation of a system is known to the tester.
B. The internal operation of a system is completely known to the tester.
C. The internal operation of a system is only partly accessible to the tester.
D. Only the external operation of a system is accessible to the tester.
Answer: D
NEW QUESTION 721
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
A. Read the first 512 bytes of the tape.
B. Perform a full restore.
C. Read the last 512 bytes of the tape.
D. Restore a random file.
Answer: B
NEW QUESTION 722
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a ____ database structure instead of SQL’s ____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A. Strict, Abstract
B. Simple, Complex
C. Relational, Hierarchical
D. Hierarchical, Relational
Answer: D
NEW QUESTION 723
What is the purpose of DNS AAAA record?
A. Address prefix record
B. Address database record
C. Authorization, Authentication and Auditing record
D. IPv6 address resolution record
Answer: D
NEW QUESTION 724
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
A. Intrusion Detection Systems can easily distinguish a malicious payload in an encrypted traffic.
B. Intrusion Detection Systems can examine the contents of the data in context of the network protocol.
C. Intrusion Detection Systems can be configured to distinguish specific content in network packets.
D. Intrusion Detection Systems require constant update of the signature library.
Answer: A
NEW QUESTION 725
During an Xmas scan, what indicates a port is closed?
A. RST
B. SYN
C. ACK
D. No return response
Answer: A
NEW QUESTION 726
Which command can be used to show the current TCP/IP connections?
A. Netsh
B. Net use connection
C. Netstat
D. Net use
Answer: C
NEW QUESTION 727
You are performing information gathering for an important penetration test. You have found pdf, doc, and images in your objective. You decide to extract metadata from these files and analyze it. What tool will help you with the task?
A. Armitage
B. Dmitry
C. Metagoofil
D. CDPSnarf
Answer: C
NEW QUESTION 728
You have several plain-text firewall logs that you must review to evaluate network traffic. You know that in order to do fast, efficient searches of the logs you must use regular expressions. Which command-line utility are you most likely to use?
A. Relational Database
B. MS Excel
C. Notepad
D. Grep
Answer: D
NEW QUESTION 729
This phase will increase the odds of success in later phases of the penetration test. It is also the very first step in Information Gathering and it will tell you the “landscape” looks like. What is the most important phase of ethical hacking in which you need to spend a considerable amount of time?
A. network mapping
B. footprinting
C. escalating privileges
D. gaining access
Answer: B
NEW QUESTION 730
When you are collecting information to perform a data analysis, Google commands are very useful to find sensitive information and files. These files may contain information about passwords, system functions, or documentation. What command will help you to search files using Google as a search engine?
A. site:target.com filetype:xls username password email
B. domain:target.com archieve:xls username password email
C. inurl:target.com filename:xls username password email
D. site:target.com file:xls username password email
Answer: A
NEW QUESTION 731
……
Download the newest PassLeader 312-50v10 dumps from passleader.com now! 100% Pass Guarantee!
312-50v10 PDF dumps & 312-50v10 VCE dumps: https://www.passleader.com/312-50v10.html (772 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New 312-50v10 dumps PDF: https://drive.google.com/open?id=1_ULihyLPLTBI_LfyL2UePVvTPFp3Vws-
P.S. New 312-50v9 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpdnh4LVZhSV9hYm8
P.S. New 312-49v9 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpSnJrVWZSSFFMVVE